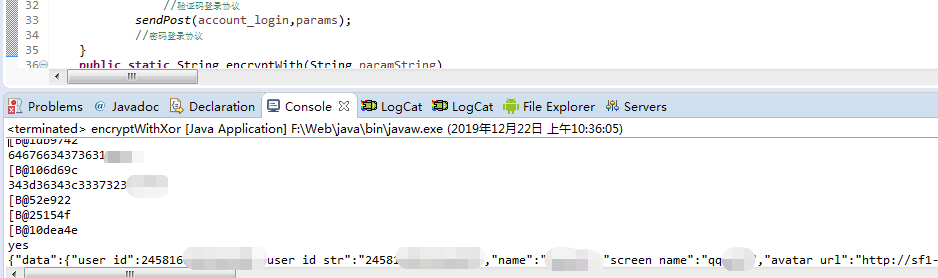
抓包分析
手机登录处抓包
发现mobile参数
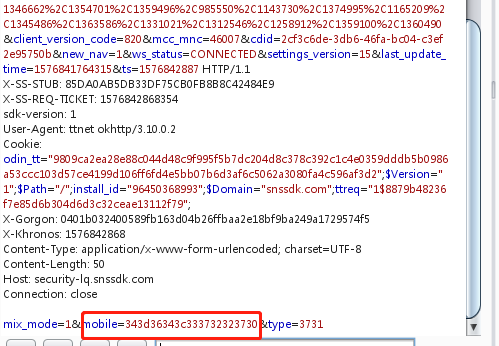
逆向分析算法
这里我先把apk解压,发现里面有7个dex,然后用d2j-dex2jar工具把dex文件转换成jar
1 | d2j-dex2jar *.dex |
用jd-gui打开全部包,然后全局搜索mobile
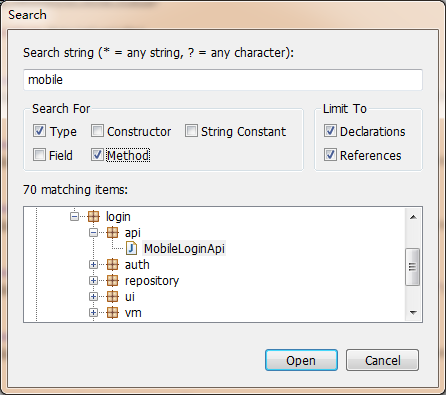
这里之所以不选择jadx的原因是其搜索太慢,有点麻烦,可读性也不及jd-gui,不过jd-gui最大的缺点是不能直接看到搜索出来的代码,要看类名判断关键代码的位置,然后点击类名才能看到代码,不过我一般看类名就能猜出关键代码的位置,所以这里选择了MobileLoginApi这个类名
点进去查看函数方法
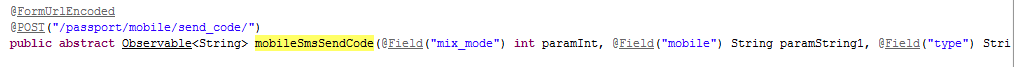
这里看到mobilesmsendcode这个方法名,然后全局搜索这个方法名
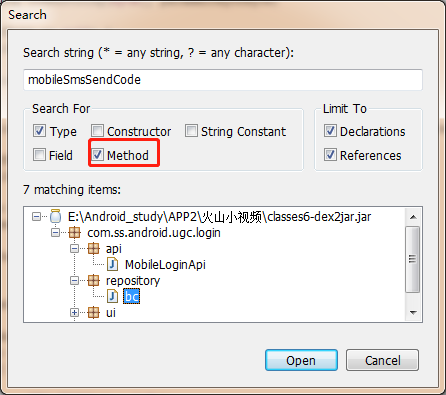
进入这个bc类
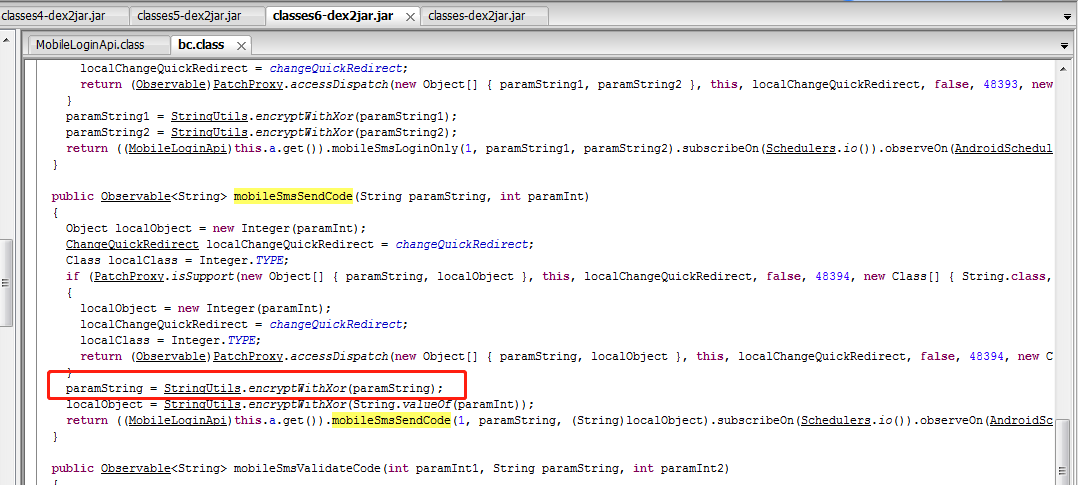
这里调用了MobileLoginApi的方法,找到关键加密函数StringUtils()
继续进入这个类
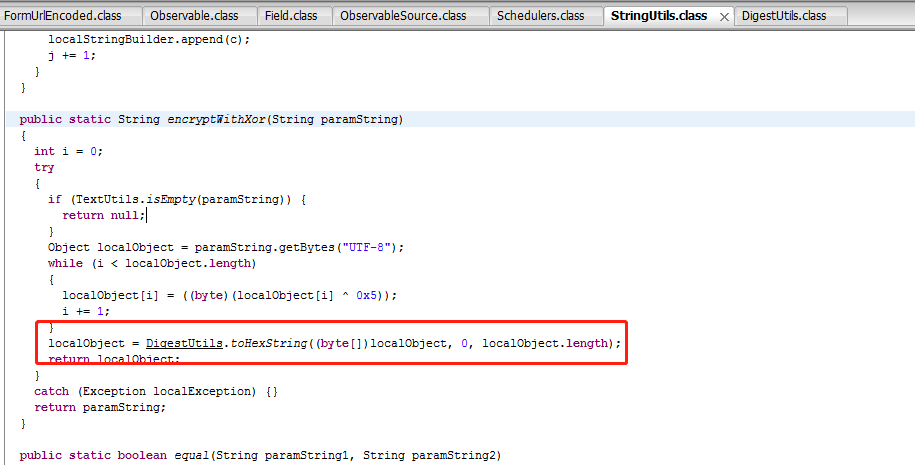
这里是将手机号码getByte(”utf-8”)后再将数组的每一位都与0x5异或,然后再调用DigestUtils类的toHexString方法加密,下面进如这个类
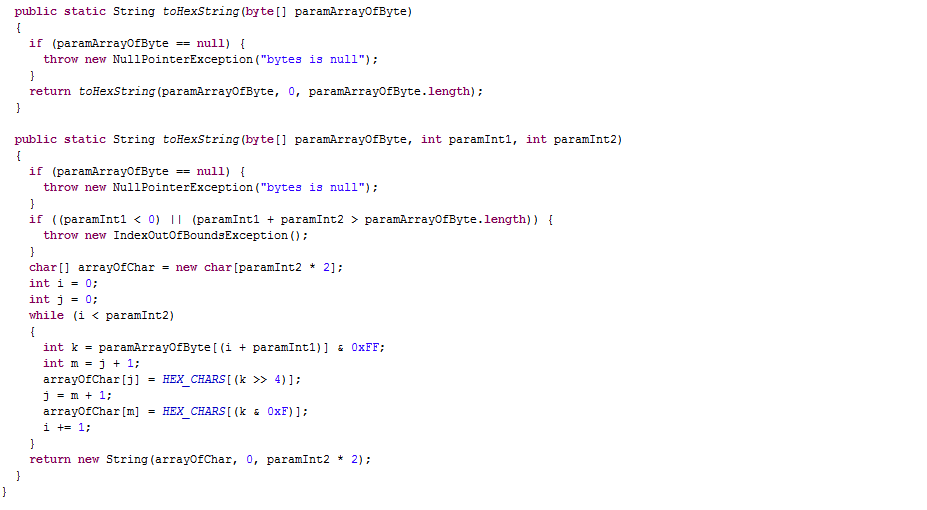
这里进行一系列的加密操作,接下来我们直接重构他的算法
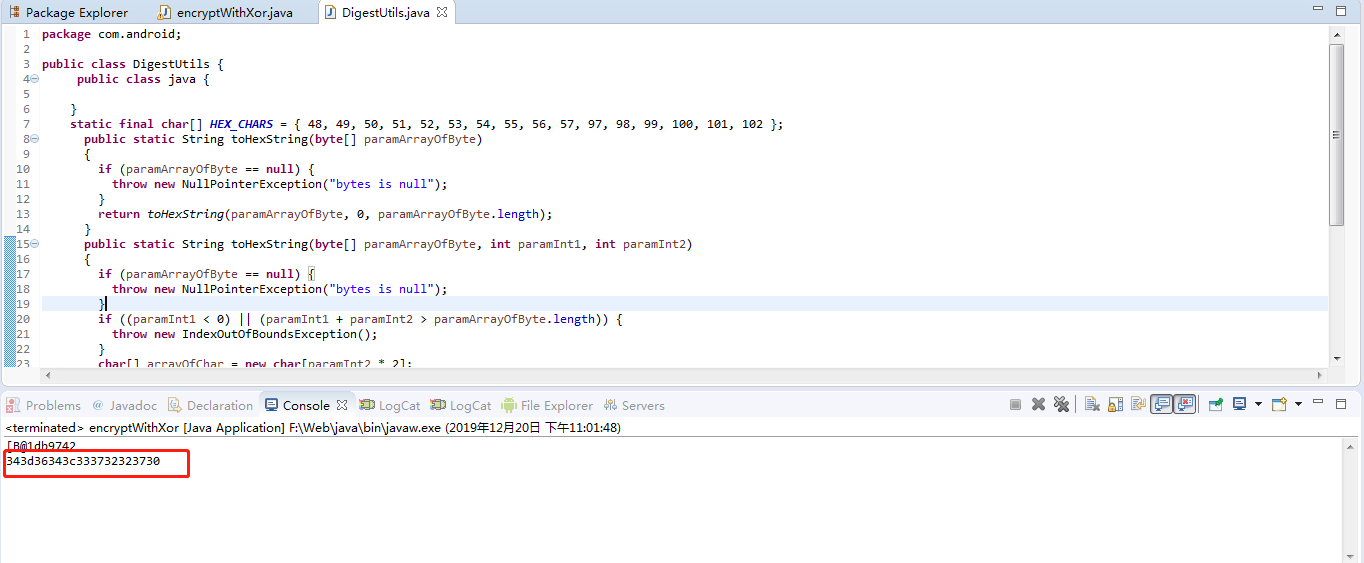
这里直接调用函数,输入手机号码参数,直接输出了加密后的手机值.
输入验证码,点击抓包
这里是短信登录的接口
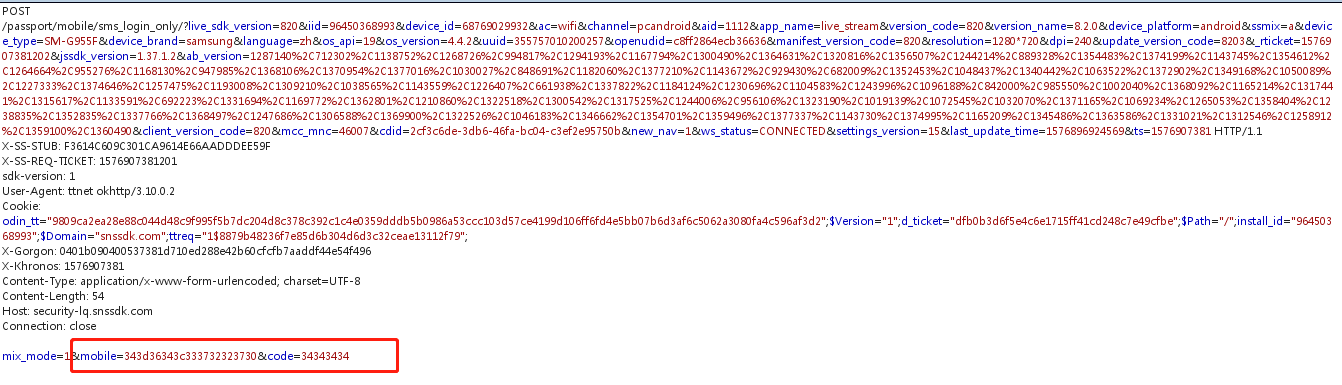
逆向查看发现这里的加密算法跟手机号的加密算法是一样的
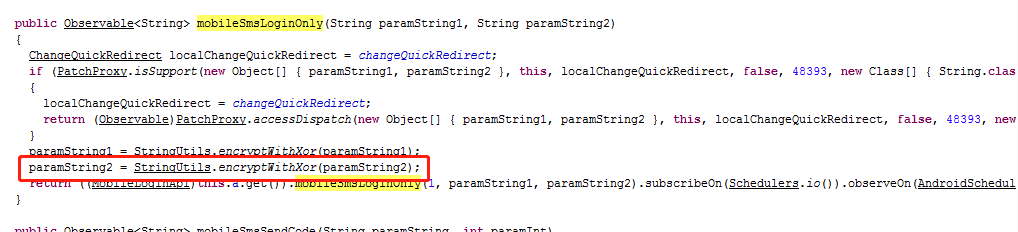
后来再继查找发现原来密码登录的加密算法也是一样的
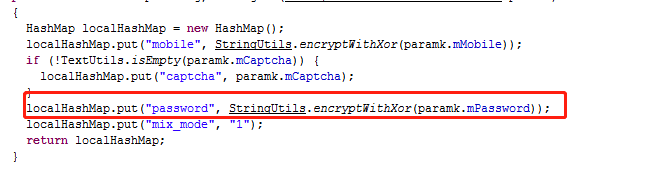
下面用java项目写一个模拟发送验证码、短信登录和密码登录的协议,代码如下
1 | package com.android; |
1 | package com.android; |